- Download Facebook Brute Force Cracker Software
- Brute Forcing Hacking Free
- Hydra Brute Forcing Download
- Brute Force Hacking Apps For Facebook
Facebook Brute Force Cracker. Brutus password cracker bangs against network services of remote systems trying to guess passwords by using a dictionary and permutations thereof. It supports HTTP, POP3, FTP, SMB, TELNET, IMAP, NNTP, and more. POP3 Brute-Force Protection. Create A Brute Force Password Cracker With Python.Please Subscribe and Like!!.Download Lin.
How to Hack Facebook Account without phishing and brute force How to install: – Download, extract and run.exe file, (If your antivirus blocking file, pause it or disable it for some time.) – Choose destination folder. How to Use: Open destination folder and locate file notes.txt, open it and read step by step. ESoftTools Excel Password Recovery is a very helpful program for those who lost or forgot their MS Excel file opening password or excel worksheet password. This software moves you in 100% comfort zone by utilizing its smart technology driven Brute Force, Brute Force with Mask Attack.
A password can be a mystery term or manifestation that is usually utilized for the confirmation procedure in various programs. It is usually utilized to accessibility records and possessions. A key key shields our records or resources from unapproved find to.What is the Password Cracking?Secret key breaking is the way of taking a chance or recouping a password from putting away places or from info transmission structure. It is used to get a secret term for unapproved gets to recover an unnoticed security password. In entry screening, it is usually used to check the safety of an program.
As of late, PC software engineers have got been trying to guess the key essential in much less period. The greater component of the key is to sign in with each imaginable mix of think words. On the away opportunity that the top secret word is certainly sufficiently solid with a blend of quantities, figures and unusual heroes, this breaking method may take hours to weeks or a few months.
A few of key key smashing devices make use of a term research that includes security passwords. These apparatuses are usually absolutely subject matter to the word research, so the success rate is lower.In a earlier few of decades, software technical engineers have made numerous top secret key to break the password. Each tool has its own favorite method. In this posting, we are usually covering a few of the nearly all well-known security password.What is certainly Hydra?The Hydra is a fast program login password hacking tool.
When it is contrasted and some other comparable gadgets, it demonstrates why it is usually speedier. New quests are usually anything but difficult to expose in the device. You can without significantly of a stretch include modules and update the features., Linux, Free BSD, Solaris and Operating-system Times. This device bolsters various system conferences. As of today it bolsters Asterisk, AFP, Ciscó AAA, Ciscó Auth, Cisco émpower, CVS, Firébird, FTP, HTTP-F0RM-GET, HTTP-F0RM-P0ST, HTTP-GET, HTTP-HEAD, HTTP-PR0XY, HTTPS-F0RM-GET, HTTPS-F0RM-P0ST, HTTPS-GET, HTTPS-HEAD, HTTP-Proxy, lCQ, IMAP, lRC, LDAP, MS-SQL, MYSQL, NCP, NNTP, 0racle Listener, Oracle SlD, Oracle, PC-Anywhére, PCNFS, Take3, POSTGRES, RDP, Rexec, Rlogin, Rsh, SAP/Ur3, Drink, SMB, SMTP, SMTP Enum, SNMP, S0CKS5, SSH (sixth is v1 and v2), Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPPHow will Hydra work?The Hydra is usually the greatest password cracking tool. In information safety (IT safety), is definitely the procedure of taking a chance passwords from databases that have been put apart in or are in transit inside a Personal computer platform or program.
A normal approach and the method used by Hydra and numerous other relative devices and projects can be alluded to as Brute Push. We could unquestionably total a Concise Bytes however since this blog post is definitely about Hydra we should put the challenging password estimating tool.It indicates that the plan launches a persistent barrage of passwords at a login to guess the security password. As we know, the bulk of users have weakened security passwords and all too frequently they are usually easily guessed. A little little bit of public system and the possibilities of locating the correct security password for a consumer are increased. Most people (especially those nón-IT savvy, wiIl base their ‘magic formula' passwords on terms and nouns thát they will not really easily overlook. These words are common: cherished ones, kids's titles, street address, favorite soccer team, place of birth etc.
All of this is definitely easily obtained through cultural media therefore as quickly as the hacker provides compiled this data it can become put together within a ‘security password listing'.What is certainly brute force hácking tool?It implies that the plan roll-outs a established barrage of passwords at a login to shape the security password. As we understand, the greater component the of users have got frail passwords and extremely frequently they are usually very easily speculated. A tad of sociable developing and the chances of locating the correct secret key for a customer are increased. A excellent many individuals (especially those non-IT sensible, will bottom their ‘secret' passwords on terms and things that they received't effectively overlook. These words are regular: close friends and family members, children' brands, road addresses, most cherished football group, place of delivery and therefore on. The better component of brute force hacking plan this is certainly effortlessly acquired through on the internet networking so when the developer has incorporated this details it can be gathered inside a ‘key key rundown'.Incredible force will consider the rundown that the programmer assembled and will most likely sign up for it with other identified (simple security passwords, for illustration, ‘security password1, security password2' and therefore on) and start the invasion.
Broker upon the preparing speed of the developers (inspectors) Computer, Internet association (and probably intermediaries) the savage power school of thought will deliberately experience every magic formula key until the stage when the right one is found.How to defend against Hydra ánd brute force attacks?There are several methods a system admin or network professional can defend against assaults. Here are usually a few strategies. If you can think of any others or argue with the below, let us understand in the opinion below!Disable or obstruct entry to balances when a predetermined quantity of were unable authentication tries have been reached. Consider the multi-factor or double opt-in/ log in for users. Consider applying hardware-based security bridal party in place of system-level passwords. Enforce all workers to use generated passwords or key phrases and guarantee every worker uses symbols whenever possible.
And the almost all simple - remove extremely sensitive data from the system, separate it! HackerCombat LLC is usually a information web site, which functions as a source of details for IT protection professionals across the globe. We have lived it for more than 1 year since 2017, discussing IT expert guidance and insight, in-depth analysis, and information. We furthermore educate individuals with item testimonials in different content forms.As a devoted cybersecurity news system, HC offers been providing unbiased information to protection specialists, on the countless security challenges that they arrive across every time.
NCH WavePad Keygen audio editing software is a full-featured professional audio and music editor for Windows and Mac. It allows you to record and edit music, voice and other recordings. When editing an audio file, you can cut, copy, and paste some records, then add effects such as echo, magnification, and noise reduction. RE: NCH Software Keygen v1.1, 07:17 AM #2 It's not too often that I come across a keygen with a single detection. I've looked Into the checksum, and It matches with that of the online virus scan report. Nch software keygen rar. How do you crack the 7.01 Wavepad. I tried the keygen Do I have to keep at it for hours to generate. Reply Delete.
Facebook Account Brute Force Cracker Tool For Sale
We publish data on extensive analysis, improvements on cutting-edge technologies and features with efforts from thought management. Hackercombat LLC furthermore provides a section extensively for product reviews and discussion boards.We are usually continuously operating in the path to much better the platform, and continue to lead to their durability and success.
Facebook-cracker Facebook Cracker Version 1.0 can split into Facebook Database 100% without Interruption By Facebook Firewall This program is for educational purposes just. Put on't assault individuals facebook balances it's illegal!
If you would like to crack into somebody's account, you must have the authorization of the user. Mauritania Attacker is not really responsible Whit is certainly a facebook-cracker I have got written lots of facebook hacking art icle like hack facebook using android smartphone,open source equipment,python and perl script etc. But Tóady I'will inform you about hacking in Facebook Making use of Brute force assault.
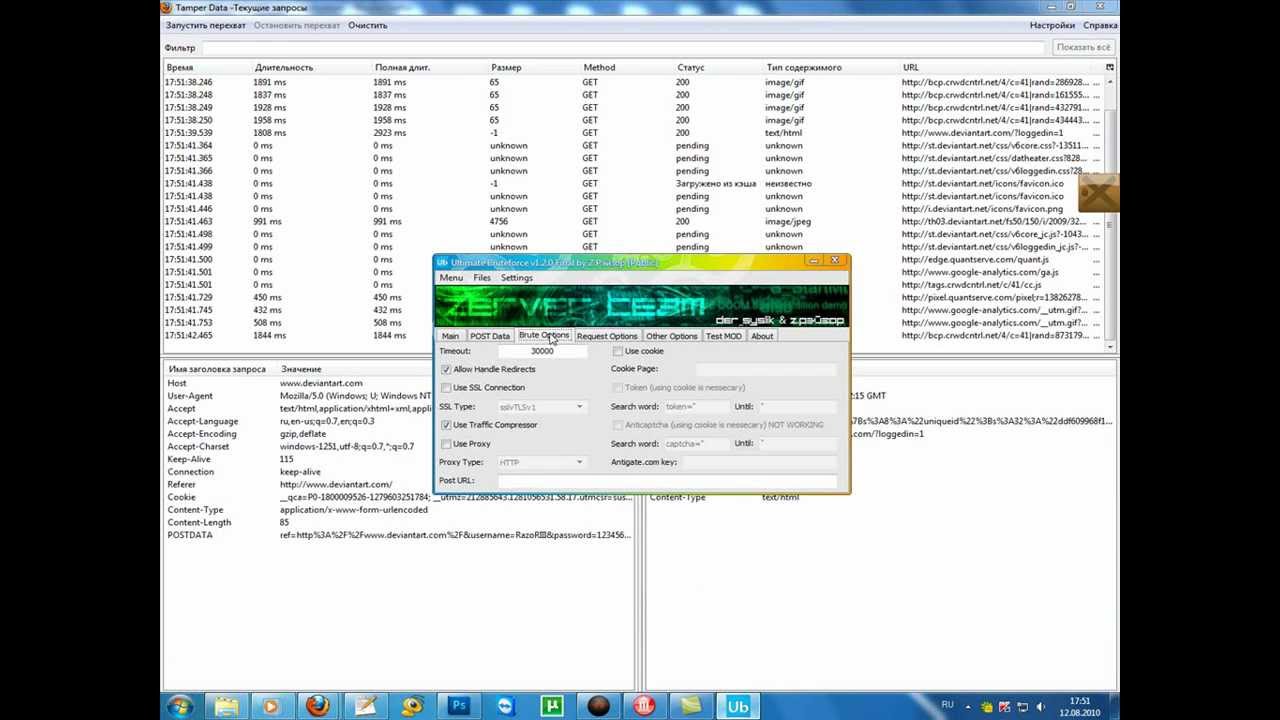
In brute force strike method,tool test all combination of password to provide gain access to of target account Incredible force strike will be the just successful technique to hack facebook account. Crack Facebook Accounts Password Making use of Brute DownloadInstall git clone compact disc facebook-cracker chmod +a facebook.py pythón facebook.py ScréenShot.
Ah!A little security alarm just proceeded to go off in my mind.If you know the telephone number that the 6 digit password is becoming sent to, you can make use of social system to tip the proprietor of the account into giving you the 6 digit program code.Illustration:'Junk! I arranged the wrong phone number for my Facebook and today I can't entry it without my protection code.
Did it obtain sent to you?' No want for infecting someone's telephone or searching endless options to brute force the program code, human ignorance is definitely the essential to hacking!(I might just create another guide).
Software Defined Radio (SDR) is the next generation of radio communications. It allows you to both transmit and receive (depending on the SDR you get) virtually any frequency or any mode from P25/DMR/DVB-S/ADS-B and more! Allowing you to track aircraft, listen to trunk radio and so much more. This entry was posted in AM, DX, Mediumwave, News, Radios, Recordings, Reviews, Software Defined Radio and tagged Airspy, BCB, broadcast band. Basics to decoding Inmarsat L-Band signals using the RSP SDR. By Mike Ladd. Note: CHECK WITH YOUR LOCAL LAWS BEFORE DECODIING ANY SIGNALS FROM THE INMARSAT SYSTEM. JAERO: A new RTL-SDR compatible decoder for Inmarsat AERO signals. The RTL-SDR is an ultra cheap software defined radio based on DVB-T TV tuners with RTL2832U chips. The RTL-SDR can be used as a wide band radio scanner. It may interest ham radio enthusiasts, hardware hackers, tinkerers and anyone interested in RF. Inmarsat software defined radio block. Inmarsat is a satellite provider that has multiple geosynchronous satellites that can be received from almost anywhere in the world at around 1.5 GHz with an RTL-SDR and appropriate antenna + LNA. Inmarsat EGC and AERO are two channels on Inmarsat satellites that can easily be decoded. Inmarsat is a communications service provider with several geostationary satellites in orbit. Inmarsat provides services such as satellite phone communications, broadband internet, and short text and data messaging services. Geostationary means that the Inmarsat satellites are in a fixed position in the sky and do not move.
- How To Play High Graphics Games Without Graphics Card
- How To Read And Hide Blue Tick For Whatsapp Messages
- What is a Keylogger & How It Works
How To Bruteforce Attack a Facebook Account 2017
Note: We are not responsible for miss using this tutorial to hack someone's password. This tutorial is only for Educational purposes and don't support anyone to do hacking..
Step By Step Tutorial To Hack a Facebook Password Easily
Things You Need For This,
- Mozilla Firefox Browser - Download It
- FireForce Addon - Download It
Download Facebook Brute Force Cracker Software

- Facebook Messenger Top 10 Tips & Tricks You Don't Know
- Super Charge Your Smartphone Within 15 Minutes | VOOC Technology
Brute Forcing Hacking Free
- Computer Performance
- Internet Speed
- OTP code number order
Here we completed the easy step by step tutorial on the topic how to easily hacking anyone's Facebook password by Bruteforcing without having any password list or wordlist. I hope you enjoyed the tutorial. If you have any doubts regarding the topic, mention it down below in the comment section. Have a blast day..
- [Undetectable] How To Hack Facebook Account By Phishing 2017
- Ultimate Top 10 Android Hacking Apps Ever In World Today
- What Is Hacking | How To Hack Using Phishing Method
- Top 10 Facebook Hacking Methods Used By Hackers In 2017
Related Articles
Hydra Brute Forcing Download
Music Profile: Crissi Cochrane - Soul…
My Top Ten Favorite Business Tools fo…
Brute Force Hacking Apps For Facebook
This post first appeared onDownload Top Full Free PC Games - TheTrickyHacker, please read the originial post:here