A RADIUS client uses a RADIUS server to manage authentication, authorization, and accounting requests that the client sends. A RADIUS client can be an access server, such as a dial-up server or wireless access point, or a RADIUS proxy.
A RADIUS Client (or Network Access Server) is a networking device (like a VPN concentrator, router, switch) that is used to authenticate users. A RADIUS Server is a background process that runs on a UNIX or Windows server. It lets you maintain user profiles in a central database. Client devices (RADIUS supplicants) and a RADIUS authentication server verify each other's identity by validating the signature on the computer and server certificates that they send one another. This authentication method uses an infrastructure that includes a RADIUS.
The Cisco Meraki MR Access Points and MX Security Appliance allow a Splash Page to be configured, requiring users to interact with this captive portal before being granted network access. One configuration option for this Splash Page is to allow authentication with an existing RADIUS server on the network, so users must enter their domain credentials to get through the Splash Page.
This article outlines the Dashboard and RADIUS configuration steps to use a RADIUS server with a sign-on Splash Page.
Supported RADIUS Attributes
When a sign-on Splash Page is configured with RADIUS server, authentication is performed using PAP. The following attributes are present in the Access-Request messages sent from Dashboard to the RADIUS server.
Note:Please refer to RFC 2865 for details on these attributes, additional notes for certain attributes are included below.
- User-Name
- User-Password
- Called-Station-ID: Contains (1) the MAC address of the Meraki access point (all caps, octets separated by hyphens) and (2) the SSID on which the wireless device is connecting. These 2 fields are separated by a colon. Example: 'AA-BB-CC-DD-EE-FF:SSID_NAME'.
- Calling-Station-ID: Contains the MAC address of the wireless device (all caps, octets separated by hyphens). Example: 'AA-BB-CC-DD-EE-FF'.
- Acct-Session-ID
- Framed-IP-Address
- NAS-Identifier
- NAS-IP-Address
- NAS-Port-Id
- NAS-Port-Type
- Service-Type
The following attributes are honored by Cisco Meraki when received in an Access-Accept or Access-Reject message from the RADIUS server to Dashboard:
- Session-Timeout: This is the maximum time in seconds that the given user's session will last. After that time, the user will need to log in (authenticate) again using their username and password. Only used in Access-Accept packets.
- Idle-Timeout: This is the idle timeout in seconds. If the user does not transfer any data on the network for this amount of time, the user's session will end and they will need to log in (authenticate) again using their username and password. Only used in Access-Accept packets. This attribute is ignored if RADIUS accounting is not enabled on the network.
- Maximum-Data-Rate-Upstream / Maximum-Data-Rate-Downstream: These are used to impose bandwidth limits, only used in Access-Accept packets. The values are the maximum rate in bits/second. See RFC 4679: vendor-specific (set Vendor-Id 3561). If these values are not present, Dashboard will use the Bandwidth limits that the user set on the Dashboard traffic shaping page as a default. If these values are set to '0', Dashboard will set the Bandwidth limit to unlimited.
Note: Maxiumum-Data-Rate-Upstream and Downstream must be specified in separate RADIUS vendor-specific attributes - if both values are specified in a single attribute, Dashboard will not honor them.
- Filter-Id: This attribute can be used to convey a group policy that should be applied to a wireless user or device. The attribute type should match that which is configured under the Configure tab > Group policies page in the Cisco Meraki Cloud Controller. The attribute value should match the name of a policy group configured on that page.
- Reply-Message: This is a message for the user that will be displayed inline on the splash page. It is allowed in Access-Accept and Access-Reject messages, but will only be shown to the user in the case of Access-Reject messages.
Note: Matching the Filter-Id RADIUS attribute with a Group Policy for sign-on splash is currently only for the MR and is in beta - please contact support to have it enabled for your networks.
Dashboard Configuration
The following instructions explain how to configure an SSID with a Splash Page using a local RADIUS server:
- In Dashboard, navigate to Wireless > Configure > Access Control.
- Select the desired SSID from the SSID drop-down menu.
- Set the Association requirement to Open (no encryption).
- Under Splash page, select Sign-on with and choose my RADIUS server from the drop-down menu:
- (optional) For Captive portal strength, choose Block all access until sign-on is complete.
- (optional) For Walled garden, choose Walled garden is disabled.
- Under RADIUS for splash page, click Add a server.
- Enter the following information:
- Host - Public IP address of the RADIUS server.
- Port - UDP port that the RADIUS server listens on for access requests, typically 1812.
- Secret - RADIUS client shared secret (if a RADIUS server has not been configured yet, select a shared secret here and make note for later).
Note: RADIUS access request messages for a Splash Page will be sourced from Dashboard, not from the local Meraki devices. As such, the RADIUS server's private LAN IP address cannot be specified here.
- Read the instructions outlined in the IP addresses section and make adjustments to network firewalls if necessary. Make sure to take note of the RADIUS client IPs listed under Help > Firewall Info.
Testing RADIUS from Dashboard
Dashboard has a built-in RADIUS test utility, to ensure that all access points (at least those broadcasting the SSID using RADIUS) can contact the RADIUS server:
- Navigate to Wireless > Configure >Access control.
- Under RADIUS servers, click the Test button for the desired server.
- Enter the credentials of a user account in the Username and Password fields.
- Click Begin test.
- The window will show progress of testing from each access point (AP) in the network, and then present a summary of the results at the end.
APs passed: Access points that were online and able to successfully authenticate using the credentials provided.
APs failed : Access points that were online but unable to authenticate using the credentials provided. Ensure the server is reachable from the APs, the APs are added as clients on the RADIUS server.
APs unreachable: Access points that were not online and thus could not be tested with.

The Test button does not exist for MX or Z-series networks.
RADIUS Configuration
While any RADIUS server can be used, the following configuration requirements are necessary for use with a sign-on Splash Page:
- RADIUS must be configured to allow PAP (unencrypted authentication) as the authentication method when you are using the Sign-on Splash page feature with a customer hosted RADIUS server.
With PAP, user credentials are sent in plain text. However, in a Meraki network, user credentials are encrypted in an SSL tunnel when sent from the clients web browser to the Meraki Cloud.
The Meraki Cloud acting as the RADIUS client sends the username and password along with other connection specific data in a RADIUS Access-request to the RADIUS server you specified in Dashboard. For security, the Meraki Cloud encrypts the password using the RADIUS shared secret and an XOR function. This ensures the users password is never transmitted in plain text.
Note: Communication between the client and Dashboard is done through the Splash Page, which is encrypted using SSL.
- Dashboard's IP addresses must be configured on the server as RADIUS clients/authenticators, with a shared secret. These IP addresses can be gathered in Dashboard from Help > Firewall Info.
Please refer to your RADIUS server vendor's documentation for configuration specifics.
Example RADIUS Server Configuration (Windows NPS + AD)
The following example configuration outlines how to configure an existing Windows 2008 server, running Network Policy Server (NPS) alongside Active Directory:
- Add Dashboard as a RADIUS Client.
- Configure a RADIUS Network Policy.
Adding Dashboard as a RADIUS Client in NPS
Since access request messages for a sign-on Splash Page are sourced from Dashboard, NPS must be configured to allow incoming requests from Dashboard's IP addresses:
- From the desktop of your Windows 2008 server, click Start > Administrative Tools.
- Click on Network Policy Server when it appears in the list.
- In the Network Policy Server console, navigate to NPS ->RADIUS clients and Servers -> RADIUS clients.
- Right click RADIUS clients and select New RADIUS client.
- Fill out the fields in the New RADIUS Client window.
- Friendly name: Unique identifier for this client.
- IP address: The IP ranges used by Dashboard (gathered in step 9 of Dashboard configuration)
- Shared Secret: Secret configured in the RADIUS server value in Dashboard (used in step 8 of Dashboard configuration). This needs to be the same for each RADIUS client you add.
- Click OK.
- Repeat these steps for each of Dashboard's IP addresses, as specified on the Access control page in Dashboard:
Configure a RADIUS Network Policy in NPS
The following instructions explain how to configure a network policy in NPS, that will allow
- From the Network Policy Server console navigate to NPS > Policies > Network Policies.
- Right click Network Policies and select New.
- On the Specify Network Policy Name and Connection Type create a Policy name and verify Unspecified is selected in the 'Type of network access server:' drop down.
- Click Next.
- On Specify Conditions click Add and append Windows Group > Domain Users group from the Windows Active Directory domain, then click OK.
- Click OK, Review the conditions, then click Next.
- On Specify Access Permission select Access granted and click Next.
- On Configure Authentication Methods make sure Unencrypted authentication (PAP,SPAP) is the only method checked and click Next.
- Click No when presented when the Connection Request Policy help pop-up appears.
- Click Next on Configure Constraints.
- On Configure Settings find the section Network Access Protection, select NAP Enforcement.
- For Auto Remediation un-check the box Enable auto remediation on client computers and click Next.
- On Completing New Network Policy click Finish.
- Prioritize the policy by Right-clicking the policy you created and selecting Move up, placing the policy above any existing deny policies.
- Review the policy values in the right side of the console:
Error: The Meraki Cloud is having difficulty connecting to your RADIUS server
When Sign-on Splash-page is used with a RADIUS server, Dashboard must be able to communicate with the RADIUS server. Dashboard, which acts as the RADIUS client, sends authentication requests (RADIUS Access Requests) to the public IP address of the configured RADIUS server.
The source IP addresses used by Dashboard may change over time. As a precaution, Dashboard periodically tests the configured RADIUS server to verify accessibility. Specifically, Dashboard sends an Access-Request message with 'meraki-ping' as the username and 'ping-test' as the password. If the RADIUS server replies with an Access-Accept or Access-Reject, Dashboard knows the server is reachable.
In the event that Dashboard does not receive a response after 6 attempts (one every 20 seconds), it will assume the RADIUS server is unreachable and an email will be sent to the Dashboard administrator.
If you received this email, please verify the following:
- If the RADIUS server is protected by a firewall, ensure that Dashboard is able to access the server through the firewall using the IP addresses and port number specified in the email. A current list of IP addresses and the port number can be found in Dashboard on the Help > Firewall Info page.
- Dashboard's IPs must be configured as RADIUS clients on the RADIUS server using the same shared secret configured in Dashboard.
- Ensure there are no additional restrictions on the RADIUS server that would prevent it from responding to Dashboard ss the test Access-Request will not contain all attributes (such as Calling-Station-ID), see below for an example message.
RADIUS Accounting with a Sign-on Splash Page

RADIUS accounting can be used with RADIUS authenticated splash pages to provide information regarding when a client was authorized through the splash page, and later had that authorization cleared/expired. These messages are sent from Dashboard to the customer's configured RADIUS server.
Note: RADIUS accounting is only available by default with 802.1X authentication. To enable RADIUS accounting for splash page as well, please contact Cisco Meraki support. RADIUS accounting is not currently available on Splash Pages for Security Appliances nor Teleworker Gateways.
Accounting Overview
When RADIUS accounting is enabled, RADIUS 'start' accounting messages will be sent whenever a client is authorized through the splash page. These start messages are sent from Dashboard, typically from the same IP address as used for the authentication Access-request message. A ‘stop’ accounting message is generated when the client's splash authorization is manually cleared or expires based on the splash frequency.
The screenshot below shows a Wireshark packet capture of an example RADIUS ‘start’ message sent by Dashboard (using an IP address of 74.50.53.101) to a RADIUS server. When the RADIUS message is expanded, there are many parameters that show the information contained within the ‘start’ message. Some data has been obfuscated for security reasons.
The screenshot below shows a wireshark packet capture of a RADIUS accounting ‘stop’ message sent by Dashboard because the Splash frequency time of 30 minutes was reached. This means the client has to log in again through the Splash Page to continue using the network.
Configuration
The following instructions outline how to enable RADIUS accounting for a sign-on Splash Page:
- In Dashboard, navigate to Wireless > Configure > Access Control.
- Select the SSID currently configured to use RADIUS with a sign-on Splash Page.
- Further down the page, set RADIUS accounting to RADIUS accounting is enabled.
Note: If this option is not available, please contact Cisco Meraki Support to have accounting enabled.
- In the RADIUS accounting servers section, click Add a server and provide the following details:
- Host - Public IP address of the RADIUS accounting server.
- Port - UDP port that the RADIUS server listens on for accounting messages, typically 1813.
- Secret - RADIUS client shared secret.
Note: RADIUS accounting messages for a Splash Page will be sourced from Dashboard, not from the local Meraki devices. As such, the RADIUS server's private LAN IP address cannot be specified here.
Radius Client Server
Data-Carrier Detect (DCD)
When enabling RADIUS accounting on a sing-on splash page with my RADIUS server, the option Enable data-carrier detect becomes available. If data-carrier detect is enabled, sessions will be revoked and accounted for whenever a client disassociates from a network. To allow clients to re-associate to the network without re-authorization, do not enable data-carrier detect. See also RFC 2866 Section 5.10.
Additional Resources
For more information on RADIUS and Splash Pages, please refer to the following documentation:
-->Applies to: Windows Server (Semi-Annual Channel), Windows Server 2016
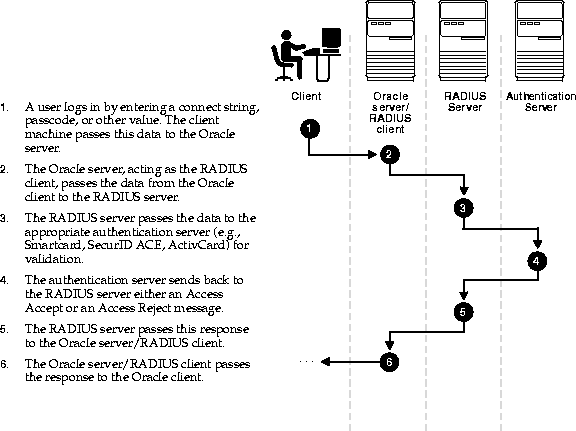
A network access server (NAS) is a device that provides some level of access to a larger network. A NAS using a RADIUS infrastructure is also a RADIUS client, sending connection requests and accounting messages to a RADIUS server for authentication, authorization, and accounting.
Note
Client computers, such as laptop computers and other computers running client operating systems, are not RADIUS clients. RADIUS clients are network access servers - such as wireless access points, 802.1X authenticating switches, virtual private network (VPN) servers, and dial-up servers - because they use the RADIUS protocol to communicate with RADIUS servers such as Network Policy Server (NPS) servers.
To deploy NPS as a RADIUS server or a RADIUS proxy, you must configure RADIUS clients in NPS.
Radius Client Tool
RADIUS client examples
Examples of network access servers are:
- Network access servers that provide remote access connectivity to an organization network or the Internet. An example is a computer running the Windows Server 2016 operating system and the Remote Access service that provides either traditional dial-up or virtual private network (VPN) remote access services to an organization intranet.
- Wireless access points that provide physical layer access to an organization network using wireless-based transmission and reception technologies.
- Switches that provide physical layer access to an organization's network, using traditional LAN technologies, such as Ethernet.
- RADIUS proxies that forward connection requests to RADIUS servers that are members of a remote RADIUS server group that is configured on the RADIUS proxy.
RADIUS Access-Request messages
RADIUS clients either create RADIUS Access-Request messages and forward them to a RADIUS proxy or RADIUS server, or they forward Access-Request messages to a RADIUS server that they have received from another RADIUS client but have not created themselves.
RADIUS clients do not process Access-Request messages by performing authentication, authorization, and accounting. Only RADIUS servers perform these functions.
NPS, however, can be configured as both a RADIUS proxy and a RADIUS server simultaneously, so that it processes some Access-Request messages and forwards other messages.
NPS as a RADIUS client
NPS acts as a RADIUS client when you configure it as a RADIUS proxy to forward Access-Request messages to other RADIUS servers for processing. When you use NPS as a RADIUS proxy, the following general configuration steps are required:
Network access servers, such as wireless access points and VPN servers, are configured with the IP address of the NPS proxy as the designated RADIUS server or authenticating server. This allows the network access servers, which create Access-Request messages based on information they receive from access clients, to forward messages to the NPS proxy.
The NPS proxy is configured by adding each network access server as a RADIUS client. This configuration step allows the NPS proxy to receive messages from the network access servers and to communicate with them throughout authentication. In addition, connection request policies on the NPS proxy are configured to specify which Access-Request messages to forward to one or more RADIUS servers. These policies are also configured with a remote RADIUS server group, which tells NPS where to send the messages it receives from the network access servers.
The NPS or other RADIUS servers that are members of the remote RADIUS server group on the NPS proxy are configured to receive messages from the NPS proxy. This is accomplished by configuring the NPS proxy as a RADIUS client.
RADIUS client properties
When you add a RADIUS client to the NPS configuration through the NPS console or through the use of the netsh commands for NPS or Windows PowerShell commands, you are configuring NPS to receive RADIUS Access-Request messages from either a network access server or a RADIUS proxy.
When you configure a RADIUS client in NPS, you can designate the following properties:
Client name
A friendly name for the RADIUS client, which makes it easier to identify when using the NPS snap-in or netsh commands for NPS.
IP address
The Internet Protocol version 4 (IPv4) address or the Domain Name System (DNS) name of the RADIUS client.
Radius Client Tester
Client-Vendor
The vendor of the RADIUS client. Otherwise, you can use the RADIUS standard value for Client-Vendor.
Shared secret
A text string that is used as a password between RADIUS clients, RADIUS servers, and RADIUS proxies. When the Message Authenticator attribute is used, the shared secret is also used as the key to encrypt RADIUS messages. This string must be configured on the RADIUS client and in the NPS snap-in.
Message Authenticator attribute
Described in RFC 2869, 'RADIUS Extensions,' a Message Digest 5 (MD5) hash of the entire RADIUS message. If the RADIUS Message Authenticator attribute is present, it is verified. If it fails verification, the RADIUS message is discarded. If the client settings require the Message Authenticator attribute and it is not present, the RADIUS message is discarded. Use of the Message Authenticator attribute is recommended.
Note
The Message Authenticator attribute is required and enabled by default when you use Extensible Authentication Protocol (EAP) authentication.
For more information about NPS, see Network Policy Server (NPS).